Chapter 2. JENKINS service account setup and certificates
Table of contents
How to set up Jenkins service account and certificates?
- Create a Jenkins Service Account with Administrative Privileges
- Set a Newly Created User as Jenkins Service Account
- Set Certificates and Keychain for the Jenkins Service Account
- Set Provisioning Profiles
In the previous chapter we went through the steps which had installed all major components relevant for JENKINS server. So, by now JENKINS server is available. Yet, we still have to do some additional configuration if we want to build objective-C projects successfully by the server.
Step 1: Create a Jenkins Service Account with Administrative Privileges
This account will be used by Jenkins service or, how it's more frequently called, Jenkins daemon. In following guidelines we will use term JENKINS daemon. Service account, in few words, is an account by which rights and privileges some tool will perform its tasks. So, in this case, when JENKINS server will try to do some builds or actually to perform any operation against operating system, it will use that service account. Technically speaking, service account is same like regular interactive accounts but it has its own specific purpose and in most cases it's not used for any other interaction. To create a new account, go to the Users & Groups tool. See picture bellow.
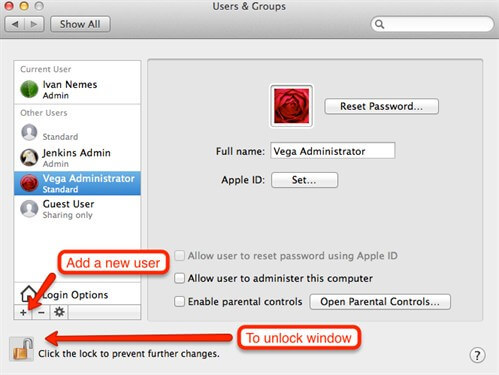
By default, the most actions in this window are locked. That's because they require administrative rights. So, unlock main window to have permissions to perform modification tasks. Now, option for adding a new user will be available as shown on the following picture. To avoid any unnecessary complications with security, grant administrative rights to the JENKINS service account. In this tutorial we will name our service account as vega worker.
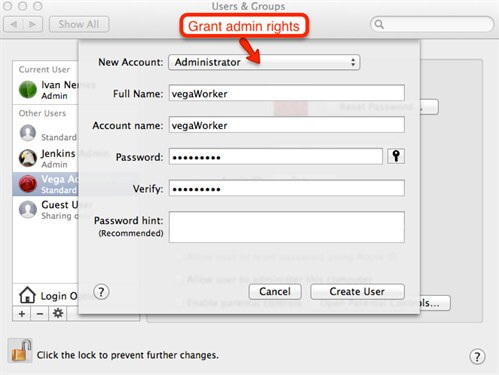
Now, when the new account is created, we can promote that account as Jenkins service account.
Step 2: Set a Newly Created User as Jenkins Service Account
To do so, first stop JENKINS daemon to be able to edit service configuration file. Open terminal and use following command to do so:
sudo launchctl unload /Library/LaunchDaemons/org.jenkins-ci.plist
Now, allow editing of jenkins-ci.plist configuration file for currently logged user. In our case it will be Vega user. Use following command (just put appropriate user name):
sudo chown -R $Vega /Library/LaunchDaemons/org.jenkins-ci.plist
Edit org.jenkins-ci.plist file through terminal by command:
sudo nano /Library/LaunchDaemons/org.jenkins-ci.plist
When this command is executed, you will see 'plist' file listing like on following picture. Change username property to be set on the newly created service account for Jenkins. In our case it will be vega Worker.
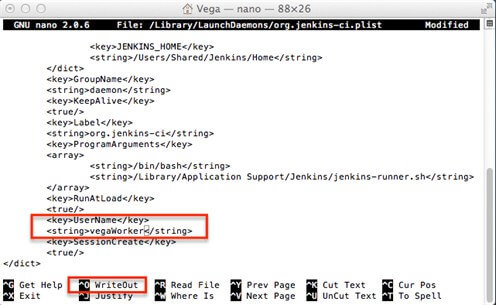
To confirm changes, useWriteOutaction at the bottom of the screen and exit 'edit' mode of 'plist'file.
Now, make the service account a file owner for entire Jenkins home directory hierarchy (by default, when installed, JENKINS is stored at location: /Users/Shared/Jenkins). Use the following command:
sudo chown -R vegaWorker: /Users/Shared/Jenkins/Home
Two steps earlier, we allowed to the currently logged on user Vega to edit JENKINS daemon configuration file, now we will revert back JENKINS service configuration ownership by command:
sudo chown -R root: /Library/LaunchDaemons/org.jenkins-ci.plist
When this is done, we can start Jenkins service once again with command:
sudo launchctl load /Library/LaunchDaemons/org.jenkins-ci.plist
Step 3: Set Certificates and Keychain for the Jenkins Service Account
Log-on to the MAC operating system with the JENKINS service account. In our case, with the vega Worker account (This is done only because we want to do some configuration steps by the JENKINS service account. When entire setup is done, we will not use any more JENKINS service account interactively). First, create a new keychain by Keychain access application. See picture bellow. Name this new keychain as ios_dev for example, and set password for it to be ios_dev.
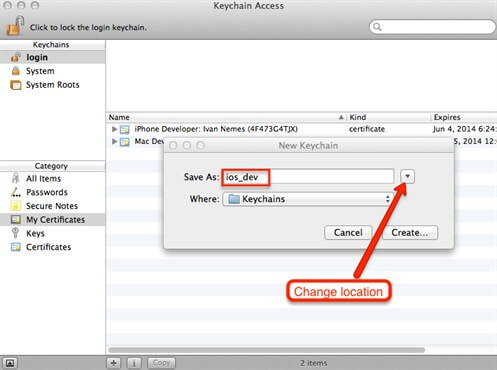
During creation of new keychain, pay attention on its location. Location is very important because it will determine does some user account can access it or not (You should treat keychain as any other file on OS X platform).
Save keychain on location: /Users/{service_account}/Library/Keychains, in our case it's: Users/vegaWorker/Library/Keychains. This way service account will have appropriate permissions to access keychain. Then, set this keychain to be a default on. Use following command in terminal for that:
security default-keychain ios_dev
Now, import all relevant certificates in ios_dev keychain. For each certificate, do double click on key and go to the access control tab. Allow using certificate by all applications. See picture bellow.
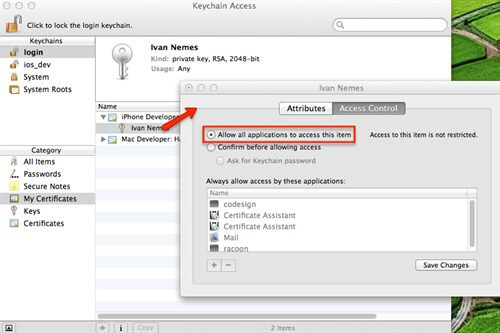
This way you will prevent OS X to show prompt dialog when certificate should be used. This is important for JENKINS jobs, because when job is started, there is no interaction between user and current build. So, if you leave that option unchecked, you will get an error during the build, because your job workflow will require prompt with credentials when it tries to use certificate and Jenkins job is no interactive task.
Step 4: Set Provisioning Profiles
Copy project relevant provisioning profiles in following directories: /Users/{service_account}/Library/MobileDevice/Provisioning Profiles (in our case /Users/vegaWorker/Library/MobileDevice/Provisioning Profiles) and /Users/Shared/Jenkins/Library/MobileDevice/Provisioning Profile. If any directory in mentioned two directory paths doesn't exist, create it manually.
Next: Chapter 3. Configuring JENKINS build jobs and security


